What are brute force attacks and how can you prevent them?
Содержание:
- Theoretical limits[edit]
- Theoretical limits[edit]
- Impossible Security
- Изменение адреса админ-панели
- Софт
- How Users Can Strengthen Passwords Against Brute Force Attacks
- Web application behavior when retrieving login data
- Examples of brute force attacks
- Locking Accounts
- Подборка словарей с сайта WirelessHack.org [Словари для взлома Wi-Fi]
- Алгоритмы хеширования
- Tools Aid Brute Force Attempts
- Unbreakable codes[edit]
- How to Defend Against Brute Force Attacks
- Unbreakable codes[edit]
Theoretical limits[edit]
The resources required for a brute-force attack grow exponentially with increasing key size, not linearly. Although U.S. export regulations historically restricted key lengths to 56-bit symmetric keys (e.g. Data Encryption Standard), these restrictions are no longer in place, so modern symmetric algorithms typically use computationally stronger 128- to 256-bit keys.
There is a physical argument that a 128-bit symmetric key is computationally secure against brute-force attack. The so-called Landauer limit implied by the laws of physics sets a lower limit on the energy required to perform a computation of kT · ln 2 per bit erased in a computation, where T is the temperature of the computing device in kelvins, k is the Boltzmann constant, and the natural logarithm of 2 is about 0.693. No irreversible computing device can use less energy than this, even in principle. Thus, in order to simply flip through the possible values for a 128-bit symmetric key (ignoring doing the actual computing to check it) would, theoretically, require 2128 − 1 bit flips on a conventional processor. If it is assumed that the calculation occurs near room temperature (~300 K), the Von Neumann-Landauer Limit can be applied to estimate the energy required as ~1018joules, which is equivalent to consuming 30 of power for one year. This is equal to 30×109 W×365×24×3600 s = 9.46×1017 J or 262.7 TWh (about 0.1% of the yearly world energy production). The full actual computation – checking each key to see if a solution has been found – would consume many times this amount. Furthermore, this is simply the energy requirement for cycling through the key space; the actual time it takes to flip each bit is not considered, which is certainly greater than 0.
However, this argument assumes that the register values are changed using conventional set and clear operations which inevitably generate entropy. It has been shown that computational hardware can be designed not to encounter this theoretical obstruction (see reversible computing), though no such computers are known to have been constructed.[citation needed]
Modern GPUs are well-suited to the repetitive tasks associated with hardware-based password cracking
A single COPACOBANA board boasting 6 Xilinx Spartans – a cluster is made up of 20 of these
AES permits the use of 256-bit keys. Breaking a symmetric 256-bit key by brute force requires 2128 times more computational power than a 128-bit key. One of the fastest supercomputers in 2019 has a speed of 100 petaFLOPS which could theoretically check 100 million million (1014) AES keys per second (assuming 1000 operations per check), but would still require 3.67×1055 years to exhaust the 256-bit key space.
An underlying assumption of a brute-force attack is that the complete keyspace was used to generate keys, something that relies on an effective random number generator, and that there are no defects in the algorithm or its implementation. For example, a number of systems that were originally thought to be impossible to crack by brute force have nevertheless been cracked because the key space to search through was found to be much smaller than originally thought, because of a lack of entropy in their pseudorandom number generators. These include Netscape’s implementation of SSL (famously cracked by Ian Goldberg and David Wagner in 1995}}) and a Debian/Ubuntu edition of OpenSSL discovered in 2008 to be flawed. A similar lack of implemented entropy led to the breaking of Enigma’s code.
Theoretical limits[edit]
The resources required for a brute-force attack grow exponentially with increasing key size, not linearly. Although U.S. export regulations historically restricted key lengths to 56-bit symmetric keys (e.g. Data Encryption Standard), these restrictions are no longer in place, so modern symmetric algorithms typically use computationally stronger 128- to 256-bit keys.
There is a physical argument that a 128-bit symmetric key is computationally secure against brute-force attack. The so-called Landauer limit implied by the laws of physics sets a lower limit on the energy required to perform a computation of kT · ln 2 per bit erased in a computation, where T is the temperature of the computing device in kelvins, k is the Boltzmann constant, and the natural logarithm of 2 is about 0.693. No irreversible computing device can use less energy than this, even in principle. Thus, in order to simply flip through the possible values for a 128-bit symmetric key (ignoring doing the actual computing to check it) would, theoretically, require 2128 − 1 bit flips on a conventional processor. If it is assumed that the calculation occurs near room temperature (~300 K), the Von Neumann-Landauer Limit can be applied to estimate the energy required as ~1018joules, which is equivalent to consuming 30 of power for one year. This is equal to 30×109 W×365×24×3600 s = 9.46×1017 J or 262.7 TWh (about 0.1% of the yearly world energy production). The full actual computation – checking each key to see if a solution has been found – would consume many times this amount. Furthermore, this is simply the energy requirement for cycling through the key space; the actual time it takes to flip each bit is not considered, which is certainly greater than 0.
However, this argument assumes that the register values are changed using conventional set and clear operations which inevitably generate entropy. It has been shown that computational hardware can be designed not to encounter this theoretical obstruction (see reversible computing), though no such computers are known to have been constructed.[citation needed]
Modern GPUs are well-suited to the repetitive tasks associated with hardware-based password cracking
A single COPACOBANA board boasting 6 Xilinx Spartans – a cluster is made up of 20 of these
AES permits the use of 256-bit keys. Breaking a symmetric 256-bit key by brute force requires 2128 times more computational power than a 128-bit key. One of the fastest supercomputers in 2019 has a speed of 100 petaFLOPS which could theoretically check 100 million million (1014) AES keys per second (assuming 1000 operations per check), but would still require 3.67×1055 years to exhaust the 256-bit key space.
An underlying assumption of a brute-force attack is that the complete keyspace was used to generate keys, something that relies on an effective random number generator, and that there are no defects in the algorithm or its implementation. For example, a number of systems that were originally thought to be impossible to crack by brute force have nevertheless been cracked because the key space to search through was found to be much smaller than originally thought, because of a lack of entropy in their pseudorandom number generators. These include Netscape’s implementation of SSL (famously cracked by Ian Goldberg and David Wagner in 1995}}) and a Debian/Ubuntu edition of OpenSSL discovered in 2008 to be flawed. A similar lack of implemented entropy led to the breaking of Enigma’s code.
Impossible Security
Brute Force and user enumeration should not be possible at the impossible security level in DVWA. There is now a lock out feature, where if there are five bad logins within 15 minutes the user account gets locked out.
If the locked out user tries to login, even with a valid password, it will say their username or password is incorrect. this should make it impossible to know there is a valid account on the system.
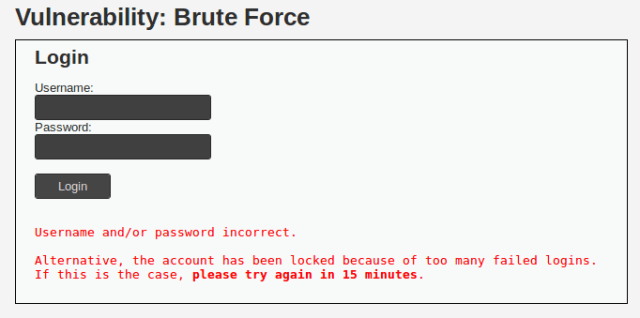
If time is not an issue we do have a couple of options here that would eventually brute force the login. We could Edit the python script we used on High Security and add a 15-minute wait after every 4 password tries. This would mean that you only try 16 diffrnet passwords a hour and if you had a huge wordlist could take you months or even years to complete.
The other option would be to use password spraying this is where you use one password against multiple users and because you are not hammering the hell out of a single user you end up not not hitting the lock outthreshold .
If you would like to see some more information about Password Sparying leave me a comment below and i will make sure i add it to the list of future posts.
Изменение адреса админ-панели
Возможно, это не самый простой и удобный способ защиты, но точно один из максимально эффективных. Изменить адрес (URL) для входа в админ панель можно вручную, если вы опытный администратор, или же при помощи специальных плагинов.
Вручную процесс состоит из нескольких этапов:
1. Переименуйте файл wp-login.php. Используйте случайную последовательность строчных латинских букв, цифры и тире. Например: some-new-page456.php
2. В получившемся файле найдите все упоминания wp-login.php и замените их на новое название.
3. Для корректной работы сайта замену необходимо проделать также в файлах: wp-activate.php, general-template.php, post-template.php, functions.php, class-wp-customize-manager.php, general-template.php, link-template.php, admin-bar.php, post.php, pluggable.php, ms-functions.php, canonical.php, functions.wp-scripts.php, wp-signup.php, my-sites.php, schema.php, ru_RU.po
После этого адрес админ панели будет располагаться по вашей новой ссылке https://site.com/some-new-page456.php. Доступ к новому файлу было бы полезно тоже ограничить и защитить паролем так, как указано выше.
Более простой способ — использование плагина, например, WPS Hide Login. После установки плагина в меню “Настройки” появится новый пункт WPS Hide Login.
Софт
Сейчас хешкрекинг в основном производится на видеопроцессорах (GPU). На обычных процессорах (CPU) брутятся только те алгоритмы, которые не реализованы под GPU. Для брута на GPU фактичeски уже стандартом стало использование программы oclHashcat, имеющей сборки как для Windows, так и для Linux, а также поддерживающей все современные видеопроцессоры — и NVIDIA, и AMD. Совсем недавно ее автор перевел программу в разряд Open Source, и теперь она доступна на GitHub, так что каждый желающий может присоединиться к работе над ее новыми версиями.
Для распределения работы этой программы между несколькими компьютерами используется оболочка hashtopus. Другим популярным GPU-брутфорсером остается нестареющий John the Ripper (JtR) в сборке Jumbo, который также имеет множество алгоритмов под все видеокарты, но для получения максимальной эффективности его желательно все-таки пересобирать под каждую конкретную конфигурацию железа.
Для работы на CPU программ гораздо больше, но самыми функциональными остаются все те же hashcat и JtR. Еще можно к ним добавить программу Hash Manager, которая больше заточена под обработку хешей в «промышленных масштабах», то есть очень крупных списков, которые не удается загрузить в другие программы. Все эти программы бесплатные, и каждый решает сам, что выбрать себе для ежедневной работы, только практика показывает, что желательно уметь владеть всем этим софтом — как правило, профессиональные хешкрекеры используют ту или иную программу в зависимости от конкретной ситуации.
Еще нужно учесть, что все эти программы консольные, не имеют встроенного GUI и, чтобы использовать их максимально эффективно, нужно уметь работать в консоли (см. врезку). А в идеале еще нужно уметь программировать командные файлы (BAT или CMD), чтобы максимально гибко настраивать работу программ. Тогда можно однократно составить для себя комплект командных файлов для разных атак, а потом, когда все настроено, весь хешкрекинг сведется к заполнению файла нужными хешами и запуску того или иного командного файла c определенными параметрами.
Консоль — райский дом хешкрекера
Самый продвинутый хешкрекерский софт — консольный и управляется либо через параметры командной строки, либо через редактирование файлов конфигурации. Но тенденция такова, что пользователи все дальше и дальше уходят от консоли, требуют графического интерфейса и наиболее популярный вопрос с форумов по работе с такими программами звучит так: «Я запустил программу, выскочило черное окно и закрылось. Что делать?» Ответ очевиден — изучать консоль.
Скорее всего, линуксоиды и так владеют навыками работы в консоли, а вот для пользователей Windows лучшим выбором будет программа FAR Manager. С ее помощью очень удобно работать со списками хешей и другими файлами. А если ее объединить с дополнительными инструментами (например, из состава программы Hash Manager), то получится просто убойный комплект, позволяющий обрабатывать любые файлы буквально за секунды.
Для этого нужно через пользовательское меню (по нажатию F2) на нужные клавиши назначить самые часто используемые инструменты — отсортировать файл, извлечь пароли из файла результатов, подсчитать количество строк в файле и так далее. После этого вся работа с нужным файлом сведется к трем действиям — встать на него курсором, вызвать F2 и нажать горячую клавишу.
После того как полностью настроишь FAR под себя — цветовой раскраской файлов, быстрыми клавишами для инструментов, быстрыми переходами в нужный каталог и так далее — вся рутинная работа хешкрекера станет очень комфортной, а значит — и очень эффективной.
How Users Can Strengthen Passwords Against Brute Force Attacks
As a user, you can do a lot to support your protection in the digital world. The best defense against password attacks is ensuring that your passwords are as strong as they can be.
Brute force attacks rely on time to crack your password. So, your goal is to make sure your password slows down these attacks as much as possible, because if it takes too long for the breach to be worthwhile… most hackers will give up and move on.
Here are a few ways you can strength passwords against brute attacks:
Longer passwords with varied character types. When possible, users should choose 10-character passwords that include symbols or numerals. Doing so creates 171.3 quintillion (1.71 x 1020) possibilities. Using a GPU processor that tries 10.3 billion hashes per second, cracking the password would take approximately 526 years. Although, a supercomputer could crack it within a few weeks. By this logic, including more characters makes your password even harder to solve.
Elaborate passphrases. Not all sites accept such long passwords, which means you should choose complex passphrases rather than single words. Dictionary attacks are built specifically for single word phrases and make a breach nearly effortless. Passphrases — passwords composed of multiple words or segments — should be sprinkled with extra characters and special character types.
Create rules for building your passwords. The best passwords are those you can remember but won’t make sense to anyone else reading them. When taking the passphrase route, consider using truncated words, like replacing “wood” with “wd” to create a string that makes sense only to you. Other examples might include dropping vowels or using only the first two letters of each word.
Stay away from frequently used passwords. It’s important to avoid the most common passwords and to change them frequently.
Use unique passwords for every site you use. To avoid being a victim of credential stuffing, you should never reuse a password. If you want to take your security up a notch, use a different username for every site as well. You can keep other accounts from getting compromised if one of yours is breached.
Use a password manager. Installing a password manager automates creating and keeping track of your online login info. These allow you to access all your accounts by first logging into the password manager. You can then create extremely long and complex passwords for all the sites you visit, store them safely, and you only have to remember the one primary password.
If you’re wondering, “how long would my password take to crack,” you can test passphrase strength at https://password.kaspersky.com.
Related articles:
Web application behavior when retrieving login data
Checking the success of authorization
How do we know if we are logged in? That is, how to understand that the password was successfully guessed? To do this, the page which is sent after the login attempt is analyzed. Sometimes we cannot know what is shown after successful authorization, because we do not have a valid account. Therefore, we can use only the inverse method: we try to enter any login and password and look at the error. For example, it can be ‘Account does not exist’. Next, the brute force compares the pages it receives, and if there is no ‘Account does not exist’, it means that the password is cracked.
Brute-force programs can also work with strings that are displayed when the input is successful.
The behavior of a web application with a successful or unsuccessful login is not limited to just displaying a message. Also, together, or even instead of displaying a message, the web application can:
- redirect (for example, in case of a successful login the user is redirected to the admin panel or to his own page);
- write the cookies (in the case of a valid login and password, the server sends cookies with session data, and based on these cookies, the web application shows the logged in user the edit button, the link to the admin panel, etc.).
And more about the displayed data — many popular web applications support many languages. This is also important to consider, because you expect to get ‘Account does not exist’ but instead it will show ‘ไม่มี บัญชี อยู่’…
Examples of brute force attacks
Brute force attacks take place all the time and there are many high-profile examples to speak of. We likely don’t even know about many bygone and ongoing attacks, but here are a few that have come to light in recent years:
- Canadian Revenue Agency (CRA): In August 2020, a credential stuffing attack resulted in the hacking of more than 11,000 accounts for the CRA and other government-related services.
- Dunkin’ Donuts: The popular coffee franchise has been ordered to pay hundreds of thousands of dollars in response to a 2015 incident where credential stuffing and brute force attacks were used to steal money through the chain’s mobile app and website.
- Alibaba: A massive 2016 brute force attack on the popular ecommerce site affected millions of accounts.
- Magento: In March, 2018, Magento had to warn users that up to 1,000 admin panels had been compromised as a result of brute force attacks.
- Northern Irish Parliament: Also in March, 2018, the accounts of several members of the Northern Irish Parliament were accessed by brute force attackers.
- Westminster Parliament: An earlier attack hit Westminster Parliament in 2017 where up to 90 email accounts were compromised.
- Firefox: It was revealed early in 2018 that Firefox’s ‘master password’ feature can be easily brute-force attacked. This means that over the past nine years, many users’ credentials may have been exposed.

Even though brute force attacks are often used by criminals, they can help to test systems. What’s more, they can offer a backup option for password recovery if other methods have been exhausted.
Locking Accounts
The most obvious way to block brute-force attacks is to simply lock out accounts after a defined number of incorrect password attempts.
Account lockouts can last a specific duration, such as one hour, or the accounts could remain locked until manually unlocked by an administrator.
However, account lockout is not always the best solution, because someone could easily abuse the security measure and lock out hundreds of user accounts.
In fact, some Web sites experience so many attacks that they are unable to enforce a lockout policy because they would constantly be unlocking customer accounts.
The problems with account lockouts are:
- An attacker can cause a denial of service (DoS) by locking out large numbers of accounts.
- Because you cannot lock out an account that does not exist, only valid account names will lock. An attacker could use this fact to harvest usernames from the site, depending on the error responses.
- An attacker can cause a diversion by locking out many accounts and flooding the help desk with support calls.
- An attacker can continuously lock out the same account, even seconds after an administrator unlocks it, effectively disabling the account.
- Account lockout is ineffective against slow attacks that try only a few passwords every hour.
- Account lockout is ineffective against attacks that try one password against a large list of usernames.
- Account lockout is ineffective if the attacker is using a username/password combo list and guesses correctly on the first couple of attempts.
- Powerful accounts such as administrator accounts often bypass lockout policy, but these are the most desirable accounts to attack. Some systems lock out administrator accounts only on network-based logins.
- Even once you lock out an account, the attack may continue, consuming valuable human and computer resources.
Account lockout is sometimes effective, but only in controlled environments or in cases where the risk is so great that even continuous DoS attacks are preferable to account compromise.
In most cases, however, account lockout is insufficient for stopping brute-force attacks.
Подборка словарей с сайта WirelessHack.org [Словари для взлома Wi-Fi]
На сайте WirelessHack.org собраны словари, которые уже некоторое время болтаются здесь и там.
В том числе, там словари:
- BIG-WPA-LIST-1 (размер 247MB)
- BIG-WPA-LIST-2 (размер 307MB)
- BIG-WPA-LIST-3 (размер 277MB)
- Darkc0de.lst (размер 17.4MB) — это был дефолтный словарь в Backtrack 5
- Rockyou.txt (размер 133MB) — дефолтный словарь в Kali Linux
- Names (размер 3.7MB) — имена и варианты имён
Кроме них ещё довольно много словарей, в общей сложности на 8.5 Гигабайт. Если вы нечасто используете словари, то рекомендуется их сжать для хранения — они представляют собой обычные текстовые файлы, которые очень хорошо сжимаются — после архивации они будут занимать примерно в 10 раз меньше места.
magnet:?xt=urn:btih:6c89df058f71559dec6c5c7c9f2cb419182b3294&dn=Collection+of+Wordlist+%28Dictionaries%29+for+cracking+WiFi+WPA/WPA2&tr=udp%3A//tracker.leechers-paradise.org%3A6969&tr=udp%3A//zer0day.ch%3A1337&tr=udp%3A//tracker.coppersurfer.tk%3A6969&tr=udp%3A//public.popcorn-tracker.org%3A6969
Торрент файл прикреплён внизу этого поста.
Алгоритмы хеширования
С одной стороны, набор актуальных алгоритмов хеширования почти не меняется со временем. Причины просты — алгоритмы хеширования паролей пользователей ОС не меняются годами, да и в интернете сотни тысяч ресурсов все еще базируются на устаревших движках, и обновление версий не происходит, несмотря на то что все новые версии форумов и CMS уже поддерживают более надежное хеширование — например, в IPB версии 4 уже сразу стоит алгоритм bcrypt. С другой стороны, небольшие изменения все-таки происходят — все больше начинает попадаться очень тяжелых алгоритмов — различные варианты PBKDF2 и тот же bcrypt, которые брутятся с мизерной скоростью даже на фермах.
Всего же известны уже сотни алгоритмов, примеры их хешей можно посмотреть здесь. Подавляющее большинство алгоритмов хеширования базируется на каком-либо из стандартных алгоритмов — MD5, SHA-1, SHA-256 и SHA-512 или на их комбинациях. Брутфорсеры давно уже поддерживают десятки таких алгоритмов в GPU-версиях и сотни алгоритмов в CPU-версиях.
Работа с любым хешем начинается с анализа его формата. Если он имеет какую-то знакомую сигнатуру (см. примеры хешей выше), то сразу понятно, каким алгоритмом его брутить. Если же хеш без сигнатуры, то анализируется движок того форума или CMS, откуда он взят. Большой список движков с описанием алгоритма в каждом из них имеется здесь. Если же движок известен, а алгоритм хеширования так и не понятен, то можно попробовать поискать в интернете дистрибутив этого движка и проанализировать его исходники, в части кода авторизации пользователей.
Ну а если так и не удается определить алгоритм, то можно спросить на форуме — например, здесь. Вдруг кто-то уже сталкивался с такими хешами?
Tools Aid Brute Force Attempts
Guessing a password for a particular user or site can take a long time, so hackers have developed tools to do the job faster.
Automated tools help with brute force attacks. These use rapid-fire guessing that is built to create every possible password and attempt to use them. Brute force hacking software can find a single dictionary word password within one second.
Tools like these have workarounds programmed in them to:
- Work against many computer protocols (like FTP, MySQL, SMPT, and Telnet)
- Allow hackers to crack wireless modems.
- Identify weak passwords
- Decrypt passwords in encrypted storage.
- Translate words into leetspeak — «don’thackme» becomes «d0n7H4cKm3,» for example.
- Run all possible combinations of characters.
- Operate dictionary attacks.
Some tools scan pre-compute rainbow tables for the inputs and outputs of known hash functions. These “hash functions” are the algorithm-based encryption methods used to translate passwords into long, fixed-length series of letters and numerals. In other words, rainbow tables remove the hardest part of brute force attacking to speed up the process.
Unbreakable codes[edit]
Certain types of encryption, by their mathematical properties, cannot be defeated by brute force. An example of this is one-time pad cryptography, where every cleartext bit has a corresponding key from a truly random sequence of key bits. A 140 character one-time-pad-encoded string subjected to a brute-force attack would eventually reveal every 140 character string possible, including the correct answer – but of all the answers given, there would be no way of knowing which was the correct one. Defeating such a system, as was done by the Venona project, generally relies not on pure cryptography, but upon mistakes in its implementation: the key pads not being truly random, intercepted keypads, operators making mistakes – or other errors.
How to Defend Against Brute Force Attacks
Brute force attacks need time to run. Some attacks can take weeks or even months to provide anything usable. Most of the defenses against brute force attacks involve increasing the time required for success beyond what is technically possible, but that is not the only defense.
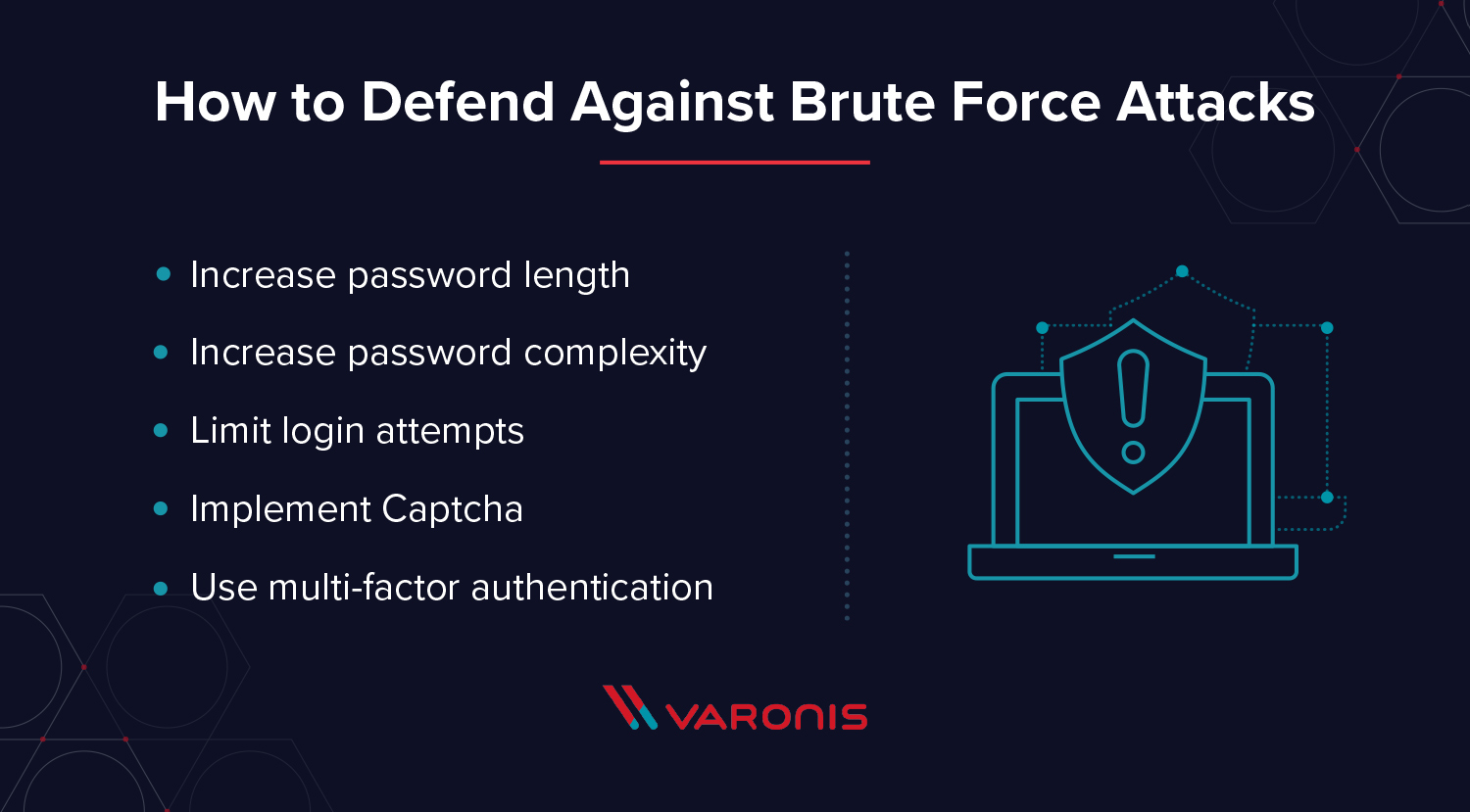
- Increase password length: More characters equal more time to brute force crack
- Increase password complexity: More options for each character also increase the time to brute force crack
- Limit login attempts: Brute force attacks increment a counter of failed login attempts on most directory services – a good defense against brute force attacks is to lock out users after a few failed attempts, thus nullifying a brute force attack in progress
- Implement Captcha: Captcha is a common system to verify a human is a human on websites and can stop brute force attacks in progress
- Use multi-factor authentication: Multi-factor authentication adds a second layer of security to each login attempt that requires human intervention which can stop a brute force attack from success
The proactive way to stop brute force attacks starts with monitoring. Varonis monitors Active Directory activity and VPN traffic to detect brute force attacks in progress. We’ve got threat models that monitor lockout behaviors (often a sign that there’s a brute force attack under way), threat models that detect potential credential stuffing, and more – all designed to detect and prevent brute force attacks before the attack escalates.
It’s better to detect an attack in progress and actively stop the attack than it is to hope your passwords are un-crackable. Once you detect and stop the attack, you can even blacklist IP addresses and prevent further attacks from the same computer.
Ready to get ahead of brute force attacks? Get a 1:1 demo to learn how Varonis detects attacks so you can stop attackers proactively.
Unbreakable codes[edit]
Certain types of encryption, by their mathematical properties, cannot be defeated by brute force. An example of this is one-time pad cryptography, where every cleartext bit has a corresponding key from a truly random sequence of key bits. A 140 character one-time-pad-encoded string subjected to a brute-force attack would eventually reveal every 140 character string possible, including the correct answer – but of all the answers given, there would be no way of knowing which was the correct one. Defeating such a system, as was done by the Venona project, generally relies not on pure cryptography, but upon mistakes in its implementation: the key pads not being truly random, intercepted keypads, operators making mistakes – or other errors.